Cyber Defense for GIC's
Operational Technology
Protecting from breaches and identifying potential attack paths using the Epiphany Intelligence Platform

Protecting from breaches and identifying potential attack paths using the Epiphany Intelligence Platform
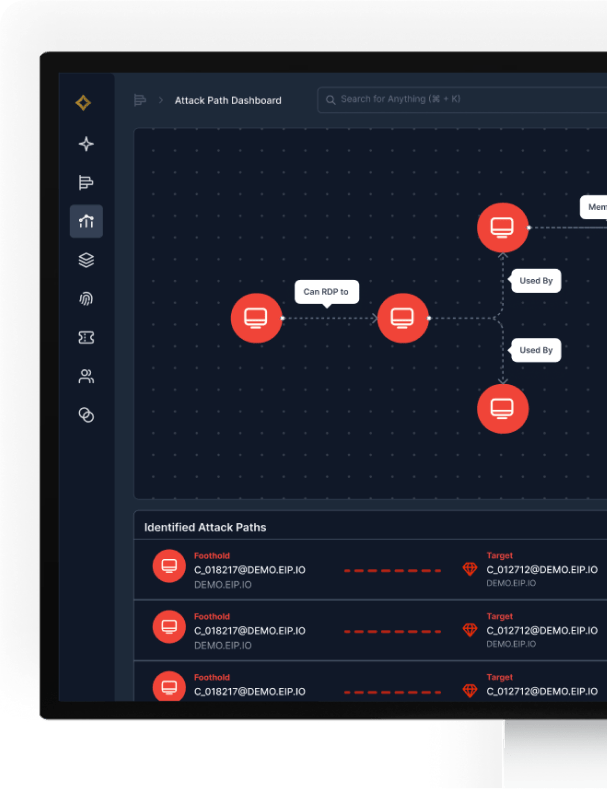
The Epiphany Intelligence Platform Identifies Attack Paths Potentially Enabled Through Computers in the GIC’s Break Rooms
A global industrial company (GIC) operating in over 80 countries with over 20,000 employees and over 200 factories needed to understand its security posture. Its ecosystem spans a broad array of holdings, technologies, and investments including public and private companies, world-class building solutions, performance materials, real estate, and next-generation solar technology.
Using the Epiphany Intelligence Platform, Reveald identified a number of issues, including several computers located in breakrooms that had the potential to enable attack paths leading to the compromise of high-value targets. Based on Reveald’s guidance, the GIC was able to remediate these issues in its IT environments and its factories’ OT environments.
A global industrial company (GIC) initially approached Reveald at the annual Black Hat USA cybersecurity conference. They were impressed with the Epiphany Intelligence Platform, saying they’d never seen a tool do attack path analysis like Epiphany. The GIC initially asked Reveald to use the Epiphany Intelligence Platform to help them prioritize their attack surface vulnerabilities that needed to be patched as the focus of a proof-of-concept endeavor. The GIC includes IT and operational technology (OT) environments in its over 200 factories.
Reveald initially performed an adversarial assessment on the GIC’s IT side by incorporating the GIC’s vulnerability scanner, Active Directory, and endpoint protection. The GIC was very impressed with the results as it immediately identified account exposures and attack paths to critical systems. This was data no other tool was able to provide. Their representative said, “if Epiphany can do the same thing on the OT side in their manufacturing factories, it’s a huge win for us and something no other platform could do.”
This led to Reveald increasing the adversarial assessment from 10,000 endpoints in the corporate side to include all manufacturing factories on the OT side.
For this adversarial assessment, Reveald used the Epiphany Intelligence Platform to analyze:
The Epiphany assessment reviewed firewalls and their rules, over 10 networks, many Claroty devices, and direct paths from the IT network to the OT network. Reveald identified a number of issues:
For each of the issues that were identified, the Epiphany Intelligence Platform provided prioritized guidance on how and where to remediate the situation. This guidance made it possible for the GIC’s IT staff to focus on the issues with the greatest likelihood for material impact, thus focusing resources for the greatest results.
The Epiphany Intelligence Platform is Reveald’s advanced exposure management software platform that enables organizations to quickly and efficiently identify, prioritize, and mitigate vulnerabilities and attack paths. It exposes the most likely attack paths to an organization’s most critical IT assets and users, and then delivers actionable recommendations on how to remove them.
Epiphany finds hidden risks in an organization’s environment that traditional scan tools can’t. It also identifies and displays attack paths between isolated networks via domain relationships and exposed services.
Epiphany uses artificial intelligence to identify areas of material risk, then prioritizes them based on several factors such as exploitability and how important a target is to the critical function of an organization. In addition to prioritizing the risks to an organization, several remediation recommendations are provided along attack paths. An IT team can take targeted action with minimal time investment on where and how to fix the problems.