
Use Case: Avoid Breaches
and Eliminate Attacks
Design a cyber strategy across IT, IoT, and OT environments to eliminate attacker potential, improve resilience, and avoid breaches.

Design a cyber strategy across IT, IoT, and OT environments to eliminate attacker potential, improve resilience, and avoid breaches.
Add customized business context (departments, system types, etc.) to device information and then group devices to this context.
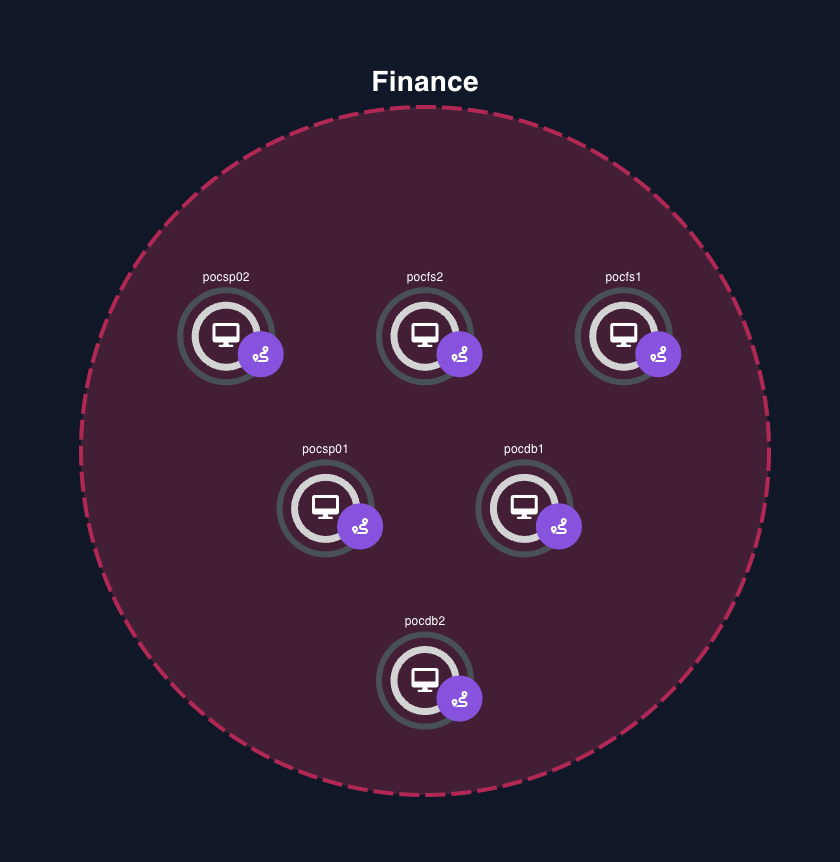
EIP BIM Configuration
Reveald’s custom reports identify top recommended actions to eliminate the exploitable attack surface threatening your business.
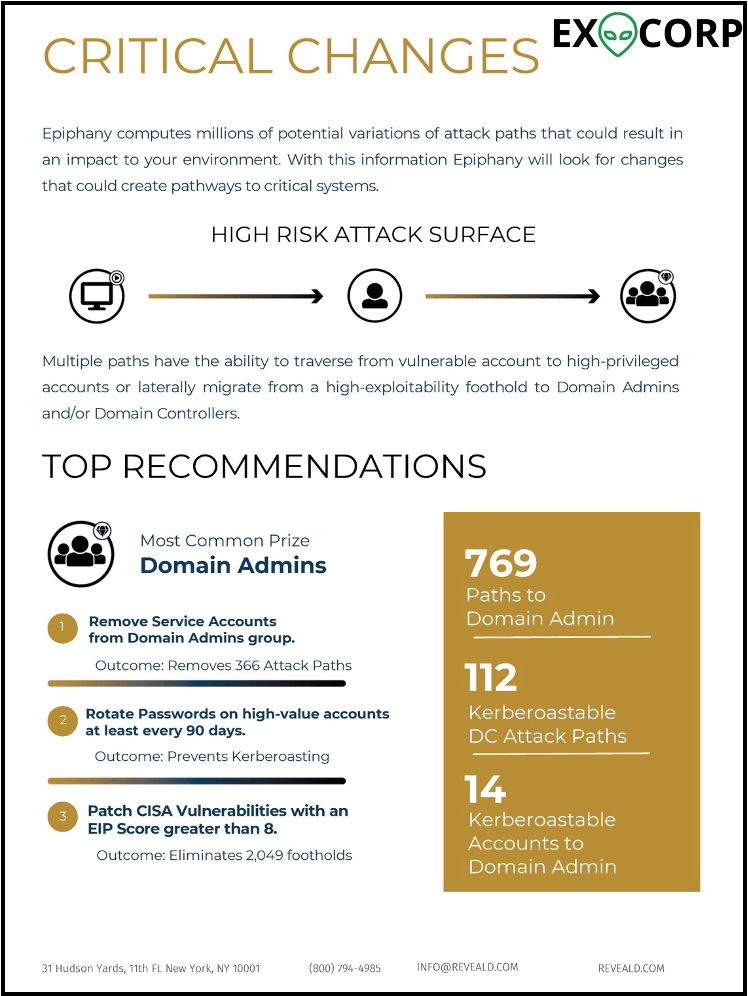
Critical Changes
Quickly identify attack paths that result in compromise of material assets.
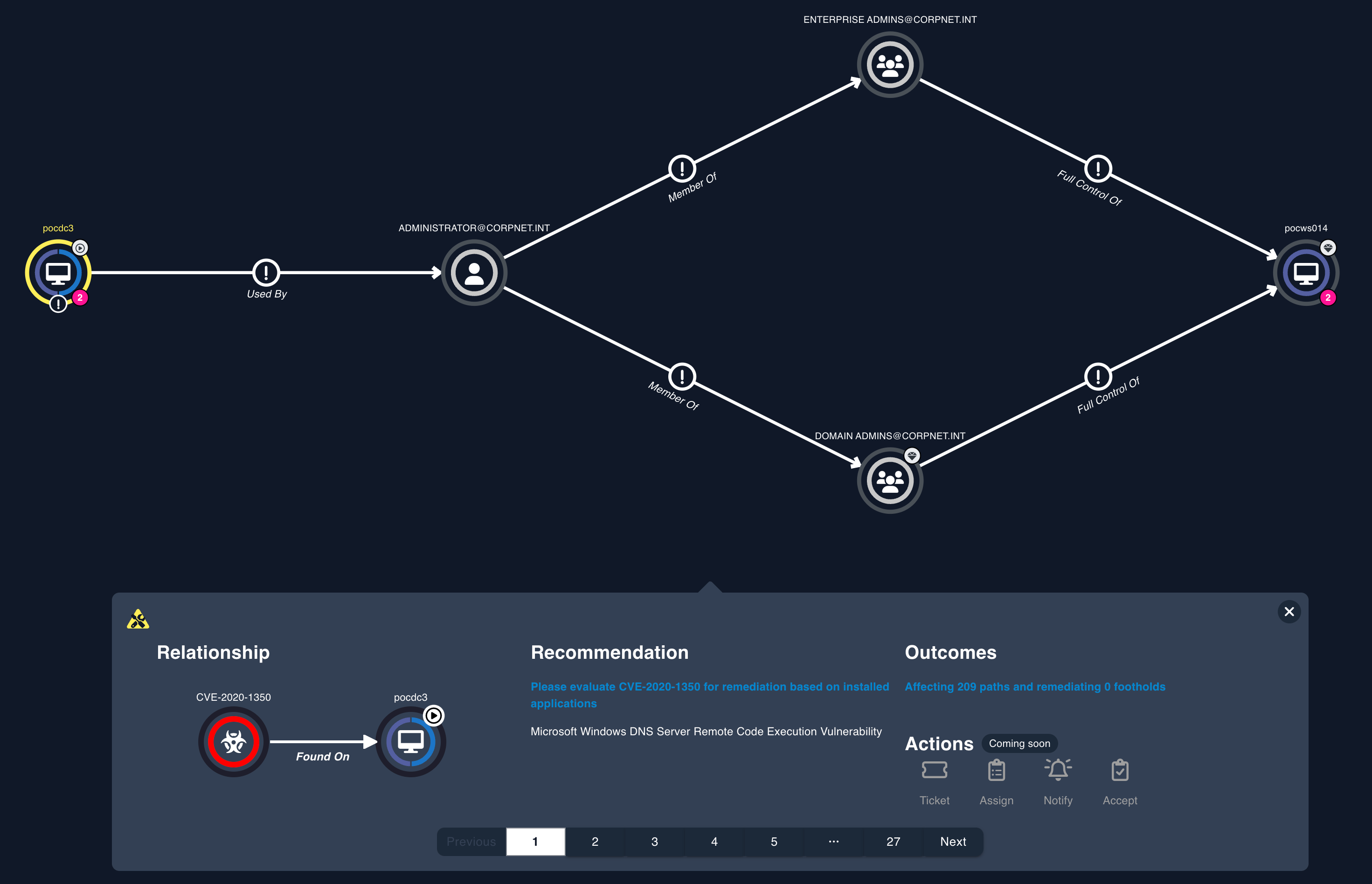
Attack Path to Critical Asset
Analyze effectiveness of cyber controls, system maintenance, access privilege management, and system configurations.
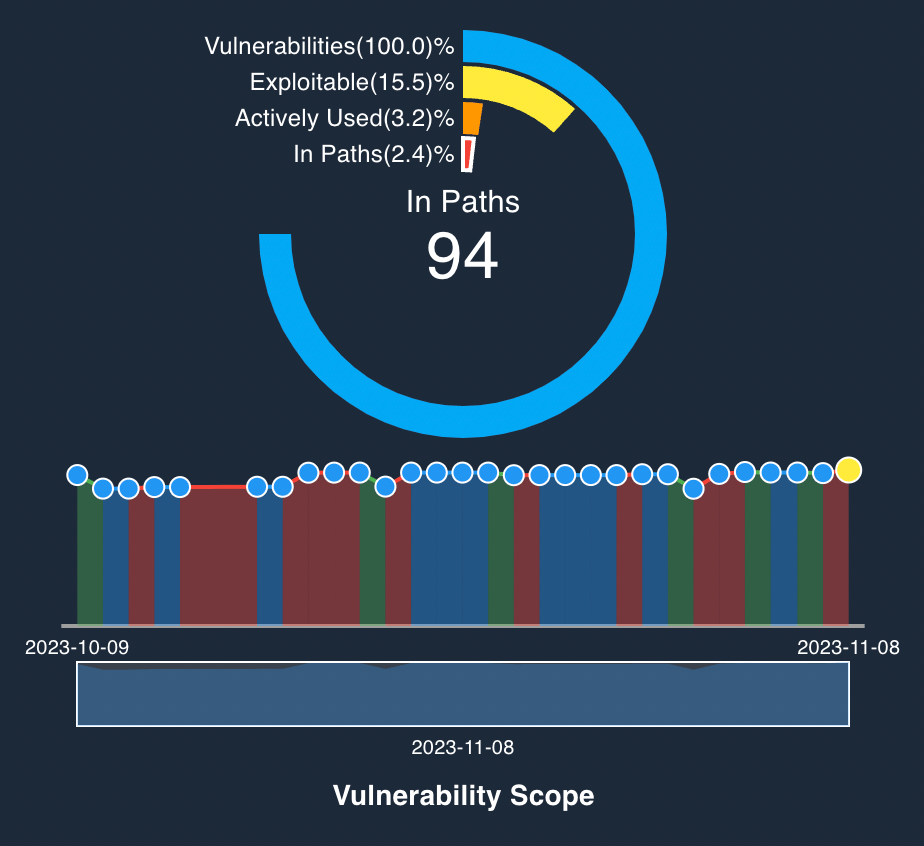
Track Material Vulnerabilities
Visualize whether each user is using required software such as antivirus or vulnerability scanners. You can’t address these issues unless you know where you lack coverage.
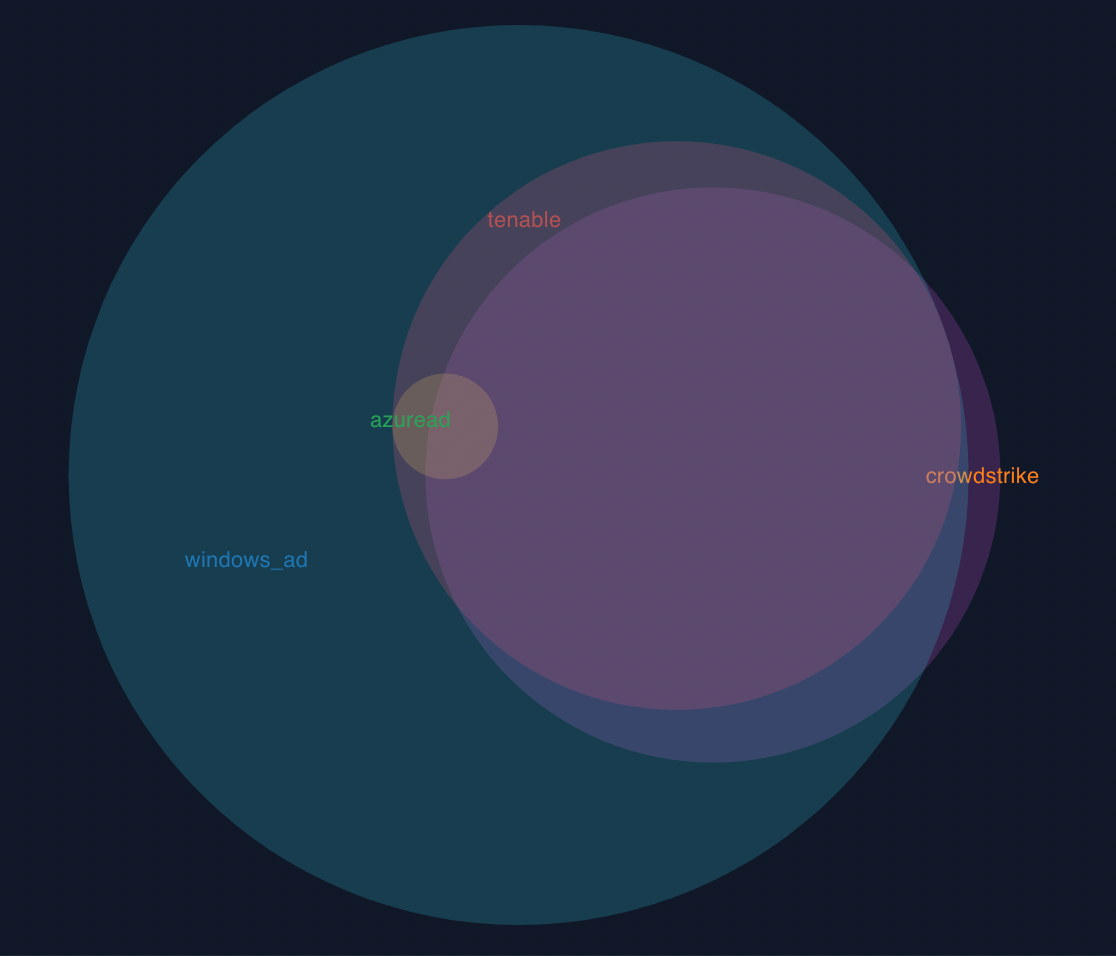
Manage Configuration Assurance
View recommendations for server handling to reduce attack surfaces.
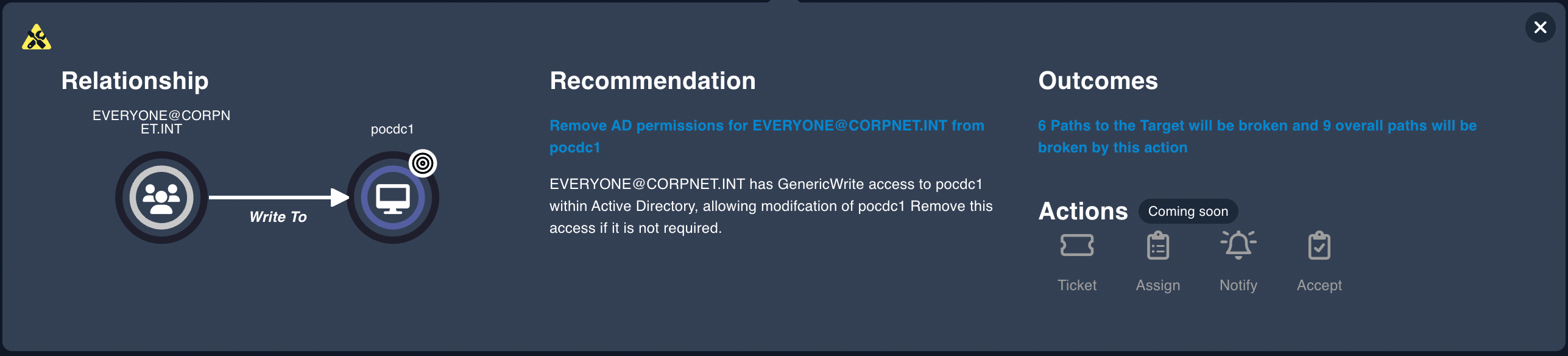
Remediation Recomendations
Reveald combines decades of cybersecurity experience with leading technology and techiques, allowing customers to shift to predictive security instead of chasing ghosts.