
Use Case: Evaluating
Mergers and Acquisitions
Cybersecurity assessments are essential in the process of mergers and acquisitions (M&A).

Cybersecurity assessments are essential in the process of mergers and acquisitions (M&A).
In the M&A process, cybersecurity assessments help to:
In addition, cybersecurity assessments can also help to:
Epiphany analyzes a potential acquisition prior to deal-closing to give you visibility into its security posture, pre-merger. Understand the acquisition’s attack surface, exploitability, and potential impact before integration occurs. An understanding of the outstanding material business risks can be factored into pre, post and acquisition costs.

Check Summary Report

Exploit Indicies
Epiphany’s exploit indices identify the aggregate potential for risks that would cause significant or material harm and the components that are driving that risk, giving you the opportunity to address issues before they are integrated into your environment.
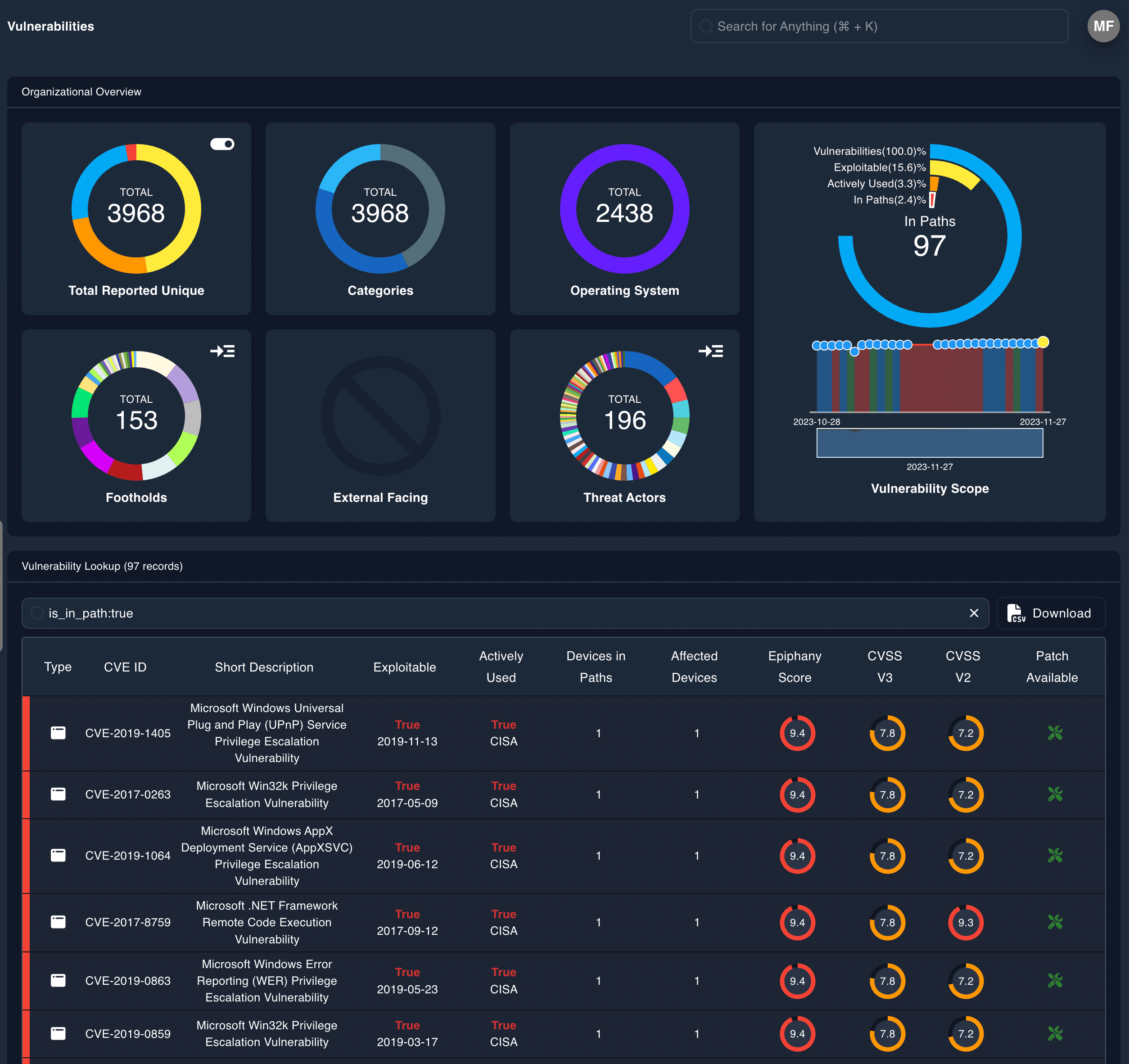
EIP Vulnerabilities
Identify specific vulnerabilities to clean up in the acquisition’s attack surface to prevent them from gaining footholds in your network post-merger.
Epiphany’s vulnerabilities report provides specific actionable information.
Reveald combines decades of cybersecurity experience with leading technology and techiques, allowing customers to shift to predictive security instead of chasing ghosts.