
Use Case: Manage Identities
Access, Auditing and Risk Management
PAM is a crucial security practice that helps organizations protect their most critical systems and data from unauthorized access.

PAM is a crucial security practice that helps organizations protect their most critical systems and data from unauthorized access.
By managing who has access to privileged accounts and systems, organizations can significantly reduce their risk of cyberattacks.
Cyber criminals typically attempt to gain access to a privileged account during the initial stages of their attack. Once the attacker has a privileged account, they have the ability to access and manipulate any data on the network. If the organization has PAM in place, the attacker will not be able to easily gain access to privileged accounts. This will make it much more difficult for the attacker to compromise the organization's systems and data.
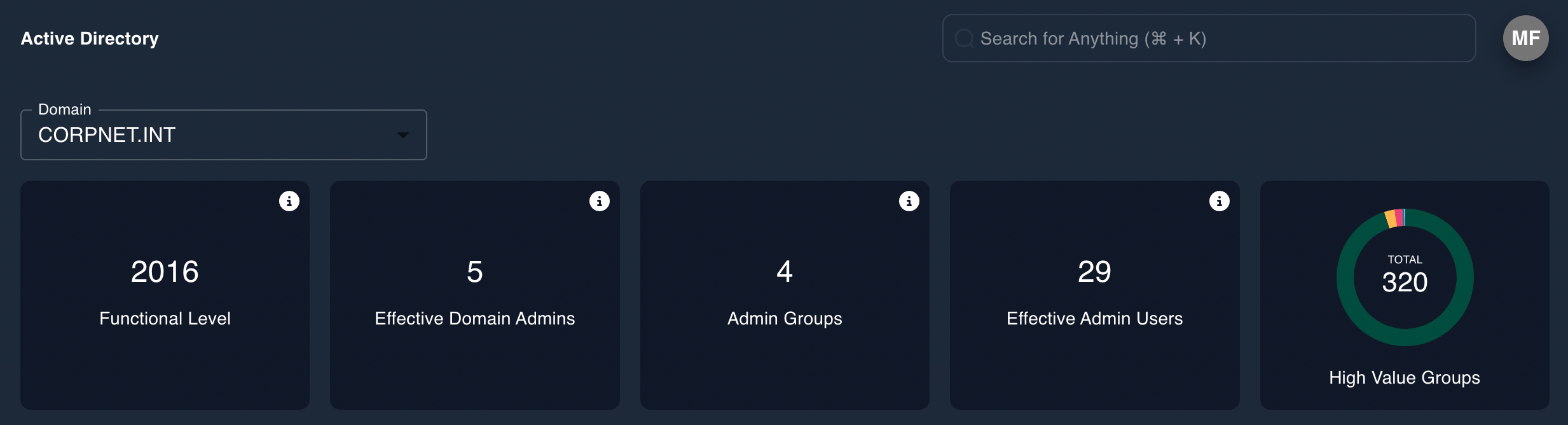
Epiphany identifies administrator users as well as “effective” administrator users who have access through excess privileges.
Reporting the number of effective administrator users is an important function of the PAM team. This ensures that privileged access is constrained to only those users whose business function require such rights. Epiphany analyzes IAM configurations to arrive at the correct information.
Additional information from the NIST Cybersecurity framework (CSF):
IAM Effective Controls
text of the second section
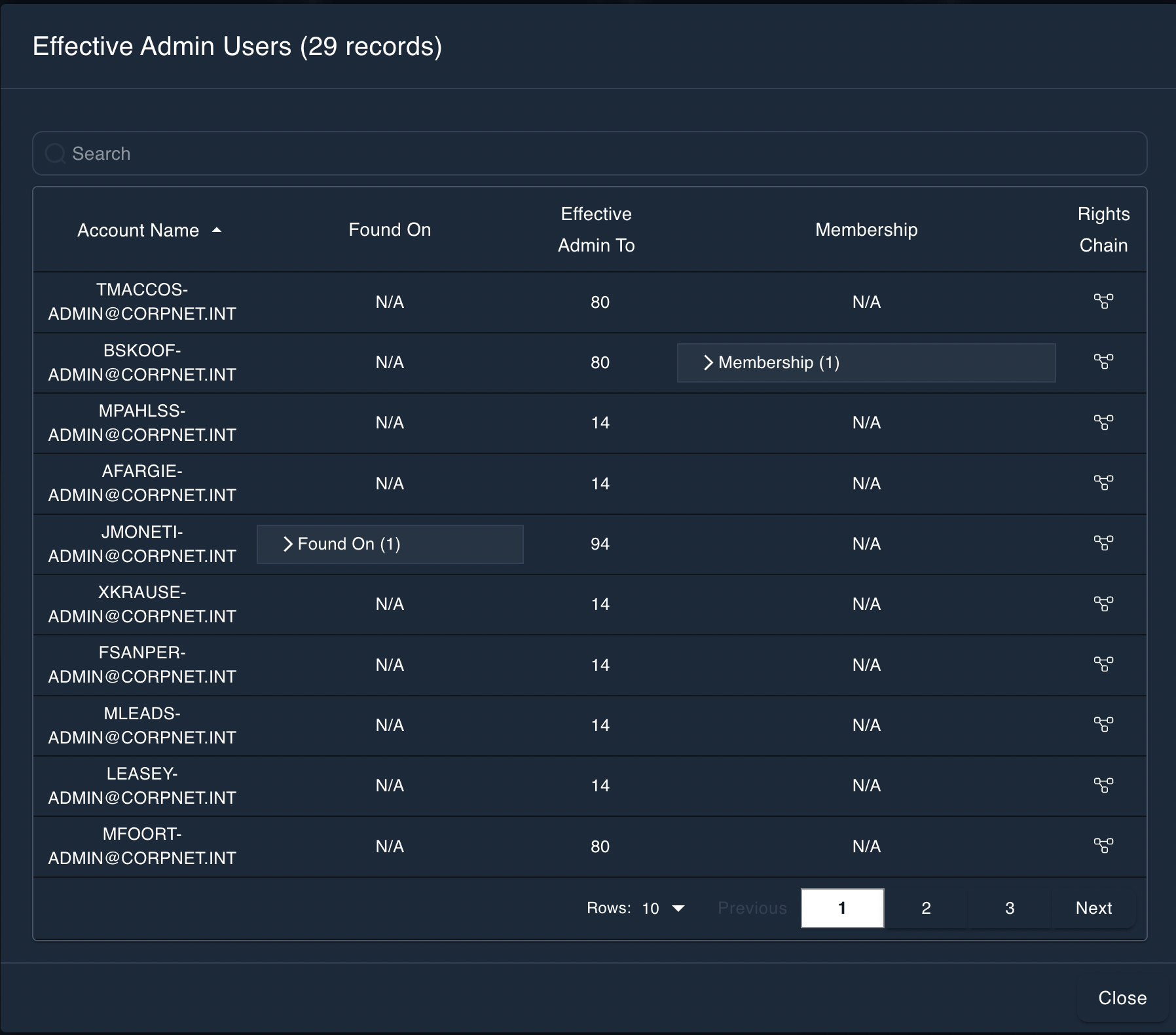
Epiphany Identifies specific users who have unnecessary elevated administrator rights.Companies should have strict control as to who is an administrator and who is not. Epiphany ensures identity managers understand who in their organization has effective administrator rights by virtue of configuration and inheritance and helps them understand and correct any misconfigurations leading to "administration right sprawl."
Additional information from the NIST Cybersecurity framework (CSF):
Effective Administrator List
Reveald combines decades of cybersecurity experience with leading technology and techiques, allowing customers to shift to predictive security instead of chasing ghosts.